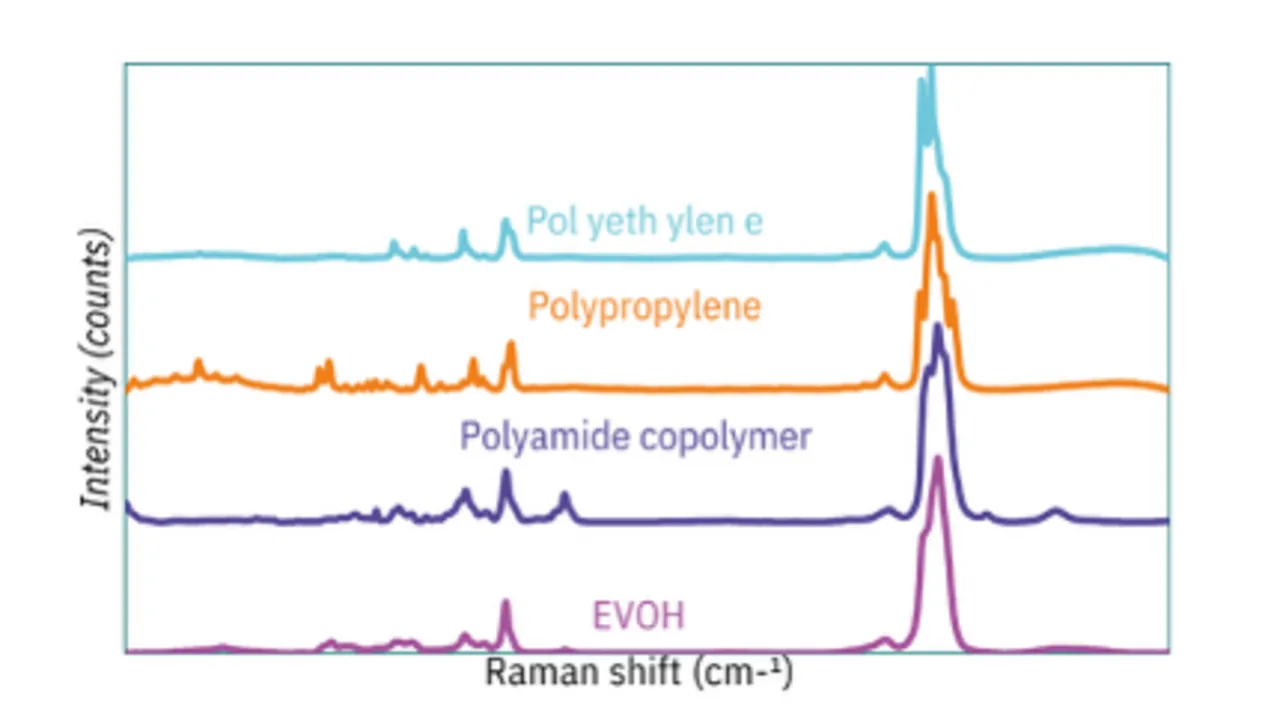
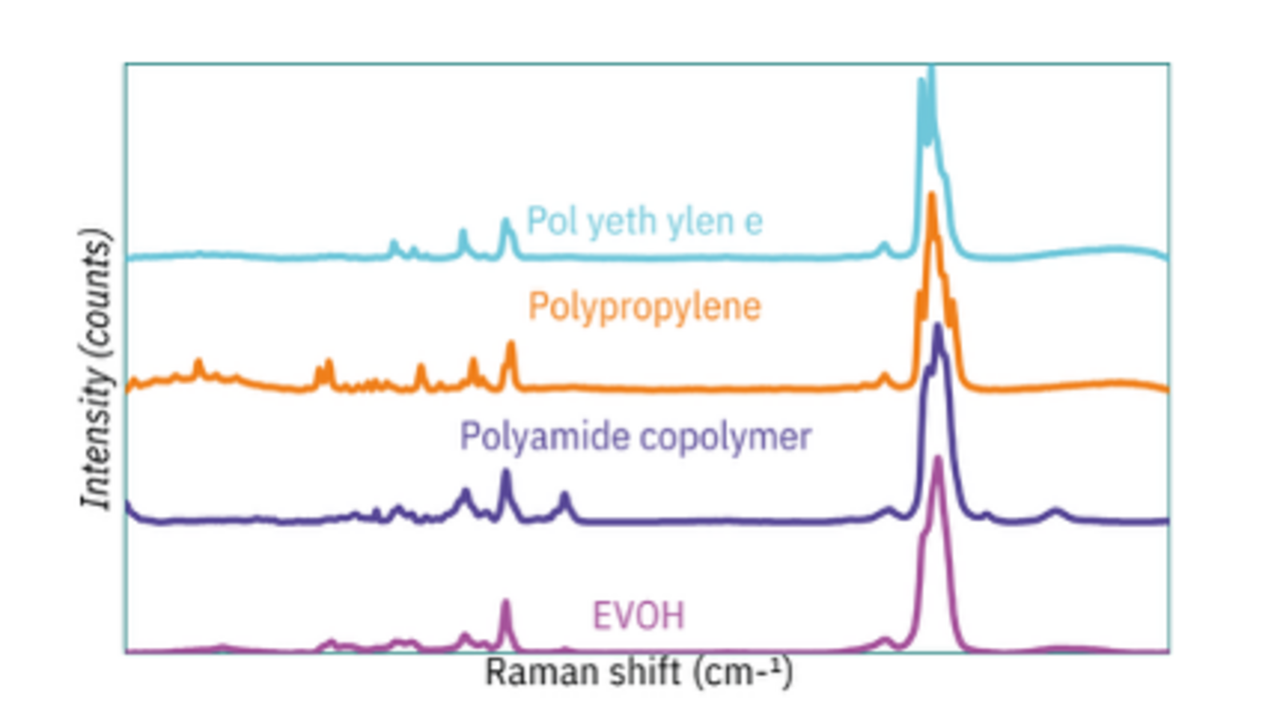
Innovative Raman Technology Unlocks the Future of Sustainable Packaging

Cybersecurity in the Modern Business Era: A Closer Look at Online Verification and Its Impact
In today’s digital landscape, the idea of online security has become as essential as the gears in an engine. With every click and every transaction, businesses – whether small or industrial manufacturing behemoths – must deal with a variety of tricky parts to keep their operations safe and trustworthy. The common sight of messages like “Verifying you are human” isn’t just a fleeting annoyance; it’s a reminder that, in our increasingly automated world, companies need to figure a path to secure their digital presence while ensuring a smooth customer experience.
The online verification process, often powered by solutions such as Cloudflare’s security systems, is a neat example of how technology is stepping in to play both the role of a gatekeeper and a facilitator. We now have to take a closer look at the broader implications this has on business operations, tax laws, industrial manufacturing, automotive sectors, and even in the electric vehicle market. Through this discussion, we are going to dig into the methods online platforms use, the necessity of avoiding nerve-racking technical failures, and what each sector can learn from these systems.
Verifying Human Presence: Tools and Technology in Action
Visiting websites today typically involves some form of human verification. Whether it’s as simple as “Verifying you are human” or more detailed multi-step processes, these techniques are designed to weed out bots and malicious auto-access. But what does this mean for the everyday user and diverse business sectors?
Cloud-Based Security and Its Role in Digital Trust
Services such as Cloudflare, which handle messages like “Ray ID: 98f0ca574a72dba3 Performance & security by Cloudflare,” have become instrumental in ensuring that online connections are secure and reliable. They essentially act as robust gatekeepers who help figure a path to filter legitimate human traffic from harmful robots. Not only does this maintain the reputation of a website, but it also prevents overloading by automated requests that can be off-putting and potentially damaging.
This system is a classic example of business tax laws in digital commerce – where operational costs can escalate if the infrastructure isn’t finely tuned to the demands of modern traffic. For small businesses with limited IT budgets, this can be a challenge. However, the reliance on cloud-based security measures has proven to be a game-changer, ensuring that both large industries and small startups can keep on top of the evolving digital threat landscape.
Securing Digital Fronts: Why Online Verification Matters
At its core, online verification using tools like CAPTCHA and security tokens is about ensuring that websites can operate smoothly, without interference from automated attacks. This is essential because a security breach not only results in immediate technical chaos but has the potential to trigger a domino effect through various systems – from the company’s backend to its financial data management systems.
For instance, in the industrial manufacturing sector, ensuring that the online systems that control production lines remain secure is super important. A breach or technical glitch could mean halting production, leading to severe economic repercussions. With the rise of Industry 4.0, where industrial manufacturing becomes more intertwined with internet-based control systems, having robust online verification is akin to a safety harness for both data and physical assets.
Small Business in a Digital Age: Challenges and Opportunities
Small businesses today face a unique blend of opportunities and challenges in the digital world. As they embrace online marketing strategies and e-commerce platforms, the requirement to secure these systems becomes more pressing than ever. Given that many small business owners may find the realm of online security a tad overwhelming at times, the role of guidance and user-friendly security systems cannot be overstated.
Implementing Simple Yet Effective Verification Tools
For most small business owners, the setup and maintenance of online security can seem like navigating through tangled issues and intimidating technical territories. The key is to adopt simple, effective verification tools that help smooth out the customer journey while ensuring safety.
- Two-step verification systems
- CAPTCHA integration
- Regular updates to firewall security
- Continuous monitoring for unusual activities
These measures, while they might appear as small distinctions in the broader picture of IT infrastructure, offer key benefits. They provide super important layers of defense against automated attacks and can be scaled up easily as the business grows.
Economic Impact and the Wider Business Ecosystem
The digital economy is not static; its successes and failures ripple across all sectors. For small businesses, disruptions in online connectivity or security breaches can have far-reaching economic consequences. Consider the following table that outlines the potential economic impacts of online security breaches on small businesses:
| Impact Area | Description | Potential Consequence |
|---|---|---|
| Customer Trust | Loss of confidence due to compromised data | Decreased sales and negative brand reputation |
| Operational Downtime | Technical issues causing website failure | Lost business days and revenue |
| Compliance Penalties | Failure to meet regulatory standards | Fines and legal costs |
| Competitive Edge | Competitors with better security measures | Loss of market share |
By addressing these potential pitfalls, small business owners can not only preserve their customer base but also protect their economic viability in a highly competitive marketplace.
Industrial Manufacturing: Keeping the Machinery and Data in Sync
Industrial manufacturing, a sector responsible for a large share of national GDP in many countries, has embraced digital transformation with open arms. The integration of digital systems into production lines means that any failure in online security can have severe ripple effects. With cyber threats growing, production plants must face yet another off-putting challenge: ensuring that automated systems remain untampered and function without hitches.
Defending Critical Infrastructure with Modern Verification Systems
One core aspect of industrial manufacturing is the interdependence between cyber systems and physical machinery. Online verification techniques help ensure that only authorized personnel or systems have access to the control units that regulate production lines. This is not just a matter of cybersecurity – it’s about preventing physical damage to machinery and risking personnel safety. In these environments, traditional verification goes far beyond keeping hackers at bay; it’s about protecting the very backbone of industrial operations.
Industrial plants now routinely implement a range of security measures, such as biometric access controls, token-based authentication systems, and regular security audits. The aim is to get around any tangled issues that might arise from unauthorized access. With these measures in place, the risk of falling prey to cyber attacks that could disrupt production is minimized significantly.
Risk Management and Cybersecurity in Manufacturing
Manufacturing companies are often working through systems that could be described as on edge due to the constant threat of cyber intrusion. To manage this risk, these companies are required to take a proactive stance in addressing online vulnerabilities. Here are some steps that are frequently implemented:
- Regular system upgrades and patching of outdated software
- Strict network segmentation to isolate critical infrastructures
- Employee training on cybersecurity best practices
- Implementation of incident response plans
These measures not only prevent cyber-attacks but also aid manufacturers in maintaining uninterrupted production, thereby safeguarding both the company’s operational output and its reputation in the market.
The Automotive Sector and the Rise of Electric Vehicles: Cybersecurity at the Intersection
The automotive industry – especially with the seismic shift towards electric vehicles (EVs) – has come face-to-face with a new set of digital challenges. As vehicles become more interconnected and reliant on software for control and navigation, ensuring secure digital communication becomes key. The verification process we see on websites is now mirrored in the automotive industry in the form of secure vehicular networks and robust encryption mechanisms.
Ensuring Safety in Connected Vehicles
Connected vehicles can be thought of as mobile computers. They employ a multitude of digital signals – from infotainment systems to engine management – that need guarding against cyber threats. Just as online platforms use verification processes to filter out malicious traffic, automotive systems implement encryption and secure communication protocols to keep hackers at bay. This makes it super important for manufacturers to embed strong cybersecurity measures right at the design stage of these systems.
For example, when a vehicle receives software updates or communicates with charging stations, there must be an automatic verification process to ensure that the data comes from a trusted source. Without this level of protection, the potential for remote hacking or unauthorized control becomes a scary possibility. Here are some key measures in this arena:
- End-to-end encryption for data transmission
- Regular over-the-air software updates with built-in security verification
- Multi-tiered authentication for access to vehicle controls
- Robust intrusion detection systems within vehicular networks
These steps represent a blend of both traditional cybersecurity strategies and innovative practices specifically designed for the automotive space. They ensure that the vehicle remains safe, not only for the driver but also for the larger ecosystem it operates within.
Electric Vehicles, Digital Transformation, and Market Readiness
The push towards electric vehicles has spurred a digital revolution within the automotive industry. New players, both established manufacturers and startups, have emerged riding the wave of digital innovation and clean technology. However, with this rise comes a set of new digital hurdles. The process of making your way through these issues can seem overwhelming, as companies must strike a balance between rapid innovation and ensuring robust security protocols.
One significant benefit of robust digital verification systems in this environment is the protection of sensitive consumer data. As customers increasingly opt for online purchases of vehicles or digital services linked to them, ensuring that customer data is secure has become a key trust-builder. Manufacturers are now working through new ways to prove their reliability with secure online systems, and each successful strategy adds a key layer of confidence to the market.
Business Tax Laws and Digital Security: An Unexpected Intersection
At first glance, business tax laws might seem like a far cry from the topic of online security. However, the two are intricately connected in our fast-paced digital age. Governments across the globe are increasingly focusing on the digital economy, devising tax policies that take into account the shifting landscape of online commerce and cyber activities.
Tax Incentives and Digital Investment Initiatives
Nations are now offering tax incentives to small businesses and larger corporations alike, encouraging them to invest in the digital security infrastructure. Such incentives can play a pivotal role in helping companies get around the nerve-racking challenges posed by high initial investments in cybersecurity measures. A few of these initiatives include:
- Tax credits for cybersecurity spending
- Rebates on cloud service expenditures
- Grants for research into advanced security protocols
- Subsidized training programs for IT staff
These measures acknowledge that a secure digital ecosystem is fundamental not only for the well-being of individual businesses but for the entire economic framework. A safer online environment reduces the risk of widespread disruption, which in turn benefits governmental revenue collection and overall economic stability.
Implications for International Trade and Digital Commerce
Businesses that operate on an international scale also find themselves working through a maze of differing tax laws and security standards. For example, what might be deemed as sufficient online verification in one country may not meet the requirements of another. This creates a layered, and sometimes confusing, set of hurdles for multinational companies.
Large industrial manufacturers and automotive companies must therefore be extra cautious. They have to ensure their cybersecurity measures are compliant with international standards and integrate seamlessly with various national regulations. Strategies include:
- Implementing globally recognized security certifications
- Adopting standards such as ISO/IEC 27001 for information security management
- Staying abreast of evolving diplomatic and trade policies related to cybersecurity
The intersection of digital security and business tax regulations is continually evolving, but one thing remains clear: a secure digital approach is key to conducting successful international trade and maintaining economic stability on a global scale.
Marketing in the Age of Cybersecurity: Building Trust in a Digital World
Marketing strategies have also had to change with the times. Gone are the days when a flashy billboard or a catchy jingle was enough. In today’s age, the digital footprint of a business is viewed as a direct reflection of its reliability. Potential customers are not just looking at the product—they’re also considering how secure and robust the online platform appears at first glance.
Consumer Perception and the Role of Secure Verification
An effective marketing strategy today needs to address the subtle details that create trust among potential customers. Integrating secure verification processes into your website isn’t just about blocking bots; it’s a signal to visitors that you take their safety seriously. Here are some considerations for marketers:
- Highlighting security features on your website
- Using customer testimonials to reinforce the perception of safety
- Ensuring that every digital interaction—from website navigation to online purchases—is streamlined and secure
- Creating content that educates customers about the measures taken to protect their data
Combining these approaches can turn every digital checkpoint into a mini brand-building exercise. Marketing is no longer just about selling a product; it’s about selling a secure experience—which in turn fosters brand loyalty in a competitive market.
The Digital Customer Journey: Balancing Security and Ease of Use
While robust security is critical, it’s equally important to ensure that the customer journey is smooth and free of unnecessary obstacles. Customers can quickly become frustrated if they encounter too many off-putting security prompts or nerve-racking verification checks. Therefore, it’s essential for companies to strike the right balance.
A useful strategy involves:
- Conducting user experience (UX) tests to identify friction points
- Using adaptive security protocols that adjust based on the risk profile
- Providing clear messaging on why security measures are in place
- Choosing technologies that combine usability with robust protection
By working through these fine points in tandem, companies can ensure that while online systems are secure, the customer doesn’t feel bogged down by excessive verification steps.
The Bigger Picture: Digital Transformation Across Industries
When we step back and look at the broader industrial landscape, one thing becomes clear: digital transformation is not just about adopting new technologies—it’s about rethinking systems to better align with modern security and efficiency standards. Whether in the automotive, small business, or industrial manufacturing sectors, digital verification systems play a super important role in ensuring operational continuity and economic resilience.
Connecting the Dots: From Online Verification to Economic Stability
Online verification is one piece of a much larger digital transformation puzzle. In many respects, it represents a microcosm of the challenges faced by businesses across diverse sectors. Here’s why:
- Trust Building: Secure verification assures customers that their data is safe. This is key to maintaining a positive brand image.
- Operational Continuity: Preventing automated attacks and data breaches means avoiding the nerve-racking scenarios where production lines or online sales come to a halt.
- Regulatory Compliance: With ever-changing business tax laws and digital regulations, robust verification systems help companies stay compliant and avoid costly fines.
- Global Competitiveness: As businesses expand beyond national borders, they must ensure that their digital security protocols are up to international standards.
In essence, whether you’re a small business owner or a head of industrial manufacturing, if you’re online, you’re managing digital risks on a daily basis. Ensuring smooth, secure verification on your website is one of the many ways you’re working through those tricky parts to build a resilient and successful operation in the digital age.
Preparing for the Future: Strategies for Continuous Improvement
Looking ahead, the landscape of online security is only set to become more woven into the fabric of everyday business operations. As cyber threats continue to evolve, so too must the strategies companies use to counter them. Some key areas to focus on include:
- Investing in Next-Generation Security Tools: Embrace tools that integrate artificial intelligence and machine learning to detect emerging threats.
- Continuous Training and Development: Ensure that your team is well-versed in the latest security protocols and can adapt to new threats.
- Collaborative Industry Initiatives: Engage with industry groups to share insights, strategies, and even best practices in maintaining digital security.
- Holistic Risk Assessments: Regularly evaluate your systems by considering both physical and digital vulnerabilities.
Through such forward-thinking strategies, companies can ensure that they aren’t just reacting to cyber threats, but actively outpacing them, staying a step ahead in this ever-evolving arena.
Conclusion: Embracing a Secure Digital Future
As we stand at the intersection of traditional business practices and the transformative power of digital technology, it is clear that securing online systems is no longer an optional extra, but a mandatory part of modern business strategy. From small businesses that rely on robust yet simple verification systems to large industrial manufacturers and automotive companies setting up secure networks for connected and electric vehicles, the need to figure a path to streamlined security is universal.
We have seen that digital verification – often experienced by everyday users as a brief check to verify they are human – is actually a crucial mechanism that supports economic stability, protects sensitive data, and builds enduring customer trust. Each sector, whether it’s marketing, industrial production, or international trade, benefits when online security measures are implemented thoughtfully and comprehensively.
Ultimately, the evolution of digital security is filled with twists and turns, but the journey is essential. Businesses that are willing to invest time, energy, and resources in securing their digital frontiers are not just shopping for technical fixes; they’re investing in their future. As emerging challenges continue to test our ability to adapt, a proactive and balanced approach to security can help carve out an era of growth, stability, and improved customer experience.
The digital landscape is rife with both opportunities and pitfalls. By acknowledging and addressing the fine points of online security – from robust verification systems and data protection measures to ensuring smooth customer experiences – companies can position themselves at the forefront of the modern business world. Embracing these strategies today will help businesses steer through tomorrow’s unforeseen challenges and ensure that, whether verifying a human presence or managing an entire production line, all operations run as seamlessly as possible.
In this interconnected era, a secure digital ecosystem is not merely a feature – it’s the backbone of modern commerce. Investing in and continually refining these protective measures is a super important step towards a future where digital interactions are both safe and efficient, ensuring that the economic engine keeps running smoothly for everyone involved.
Originally Post From https://www.plasticstoday.com/packaging/seeing-green-how-raman-spectroscopy-sheds-light-on-sustainable-packaging
Read more about this topic at
Cloudflare Turnstile | CAPTCHA Replacement Solution
Fake Cloudflare Verification Page – Almost Fell For It